Internet Security - Overview
With the usage of Internet, a number of activities take place in your computer which can be for good or bad and varies from identity thefts to people who hack into computers and steal private passwords, documents and files. The fact is that everything is online and opens us to these frauds and makes us victims, unless you have taken the necessary steps to protect your computer.
It is quite strange that till date, a lot of people don’t give much importance to Internet Security. They think that their computers are invisible, but as soon as they start using their computers for anything that involves logging onto the Internet, they are an easy prey, even for a teenaged hacker.
The following image gives you an idea of how things have changed over the years.
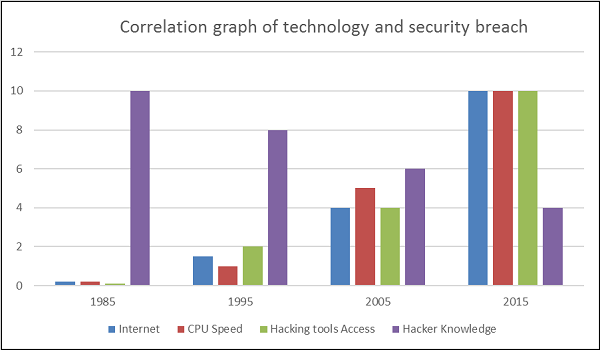
Impact from an Internet Breach
The potential losses in this “cloud” are discussed as follows.
Here is a list of some losses that can have a direct impact on you and others −
Losing Your Data − An Internet breach can swipe away all the data that you have gathered over the years.
Reputation Loss − Just think your Facebook account or business email have been hacked by a social engineering attack and it sends fake information to your friends, business partners. You will need time to gain back your reputation after such an attack. Or your webpage has been hacked and the hacker puts up an ugly picture on it, so a new customer that is visiting your webpage to get some information will see this picture named “HACKED” and the chances that he will go away without contacting you will be too high.
Identity Theft − This is a case where your identity is stolen (photo, name surname, address, and credit card details) and can be used for a crime like making false identity documents or anything else.
Internet Security - Cookies
Cookies are files, generally from the visited webpages, which are stored on a user's computer. They hold a small amount of data, specific to a particular client and website, and can be accessed either by the web server or the client computer which can be usernames, password, session token, etc.
This allows the server to deliver a page personalized to a particular user, or the page itself can contain some script which is aware of the data in the cookie and so is able to carry information from one visit to that website.
Types of Cookies
There are three different types of cookies −
Session Cookies − These are mainly used by online shops and allows you to keep items in your basket when shopping online. These cookies expire after a specific time or when the browser is closed.
Permanent Cookies − These remain in operation, even when you have closed the browser. They remember your login details and password so you don’t have to type them in every time you use the site. It is recommended that you delete these type of cookies after a specific time.
Third-Party Cookies − These are installed by third parties for collecting certain information. For example: Google Maps.
The following screenshot shows where the data of a cookie is stored and to do this, I have used a plugin of Firefox which is called Cookies Manager+. It shows the date when a cookie will expire.
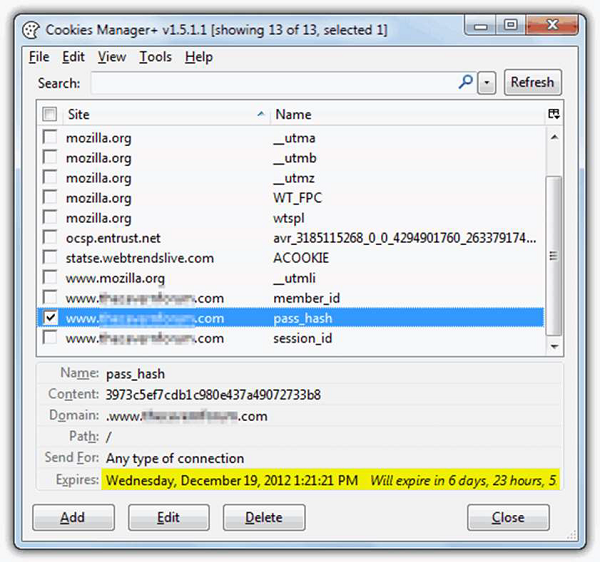
How to Block Cookies and Delete Them?
For security reasons that you think are right, the cookies can be disabled or deleted and it varies according to the Internet browsers.
Internet Explorer
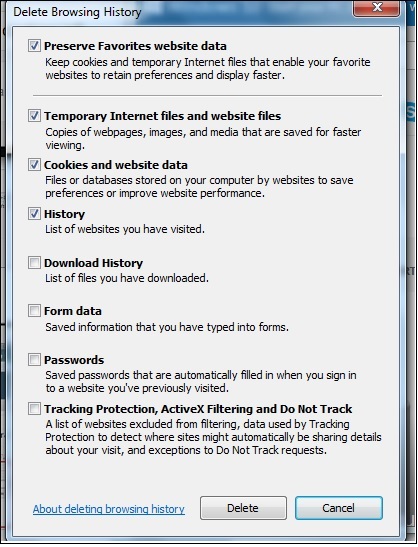
You can use the following steps to clear cookies in the Internet Explorer.
Step 1 − Press Start.
Step 2 − Click Control Panel.
Step 3 − Double click Internet options.
Step 4 − Under the General Tab, you will see 'Delete temporary files, history, cookies, saved passwords...' Click Delete.
Step 5 − The Delete Browsing History dialog box will appear, click the 'cookies' checkbox
Step 6 − Click delete button at the bottom of the dialog box
Step 7 − You will be taken back to the Internet properties dialog box. Click 'ok'.
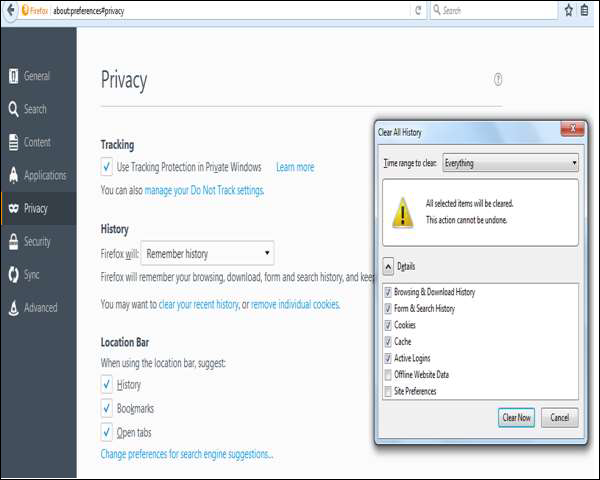
Firefox
Keep in mind that the more popular a browser is, the higher the chance that it is being targeted for spyware or malware infection.
Step 1 − Look at the top end of your Firefox window and you will see a 'Firefox' button. Click on it and click 'Options'.
Step 2 − Click on 'Privacy'.
Step 3 − You will see 'Firefox will:’ Set it to 'Use custom settings for history'.
Step 4 − Click on the 'Show Cookies' button on the right side.
Step 5 − If you want to delete cookies set by individual sites, enter the complete domain or partial domain name of the site you want to manage in the search field. Your search will retrieve the list of cookies set for that site. Click 'Remove Cookie'.
Step 6 − If you want to delete all cookies, click the top of the Firefox window and click on the Firefox button. Click on the History menu and pick out 'Clear Recent History...' Select 'Everything' for the 'Time Range to Clear' option. The click on the downward arrow located next to 'Details'. This will open up the list of items. Click 'Cookies' and make sure all the other items are unselected. Click on the 'Clear Now' button at the bottom. Close your 'Clear Recent History' window.
Chrome
Step 1 − At the top right hand side of your browser toolbar, click on the Chrome icon.
Step 2 − Click on Settings.
Step 3 − Scroll to the bottom and click 'Show advanced settings'.
Step 4 − Under 'Privacy', you will see 'Content Settings', click on it.
Step 5 − Under 'Cookies', you will see 'All cookies and site data', click on this. Please note that you can block cookies altogether from being set on your browser by clicking 'Block sites from setting any data.' Unfortunately, many websites you browse will stop working if you do this. It is better if you just periodically clear your cookies manually instead of preventing them from being set by your browser.
Step 6 − You will see a full listing of all your cookies. You can click REMOVE ALL to clear all your cookies or you can pick a particular website and clear your cookies from that site.
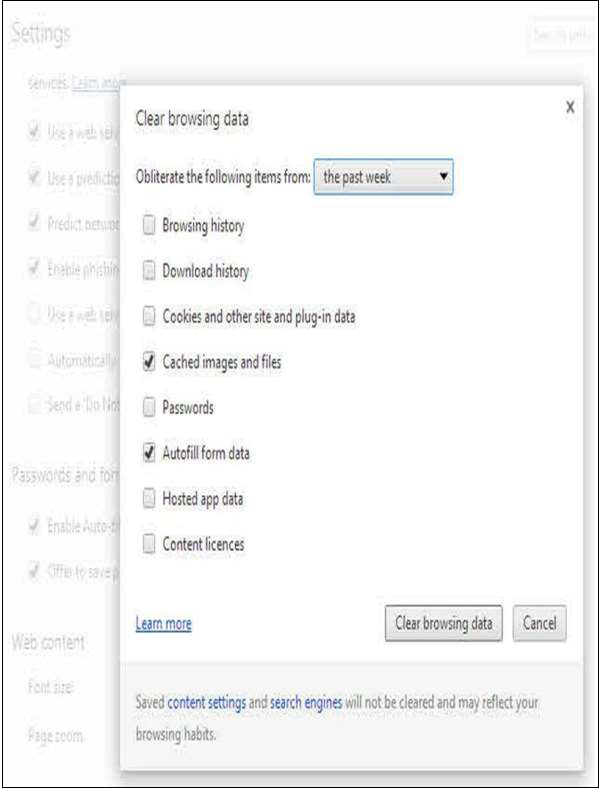
Safari
This guide is for OSX Lion −
Step 1 − Open Safari.
Step 2 − Click Safari and then on Preferences. Click on 'Privacy’.
Step 3 − Click on ‘Details’.
Step 4 − You will see a list of websites that store cookies. You can remove single sites by clicking the 'Remove' button and selecting a site. If you want clear all cookies, click ‘Remove All’.
Step 5 − When you have finished removing sites, click 'Done'.
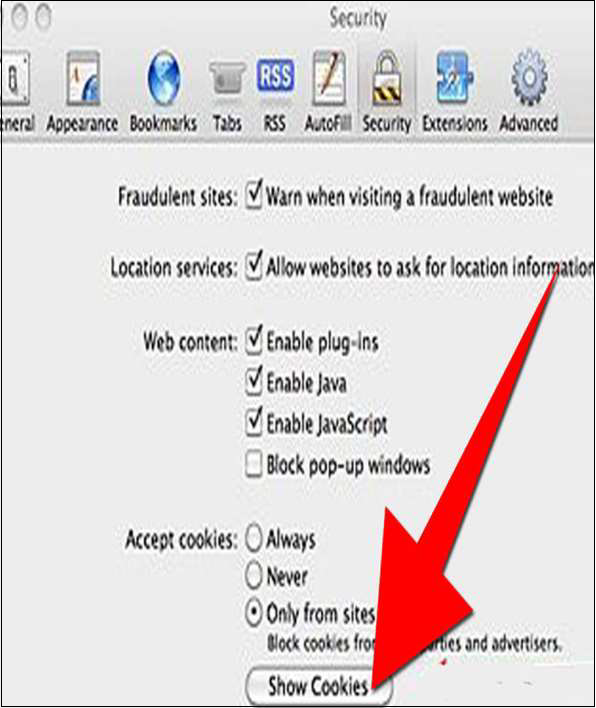
Opera
Step 1 − Click 'Settings' at the top of the Opera browser.
Step 2 − Click 'Preferences' and select 'Advanced'.
Step 3 − In the 'Advanced' screen, select 'Cookies'.
Step 4 − At this point, you can select one of three options −
- Accept all cookies (this is the default setting)
- Accept cookies only from sites you visit and
- Never accept cookies
If you block cookies, most of the sites you visit will stop working. This is usually not a good choice. Your best default choice is to accept cookies only from sites you visit. This blocks cookies set by advertising networks and other third party sites. These third party sites set cookies to track your movements across sites to enhance their ad targeting capabilities.
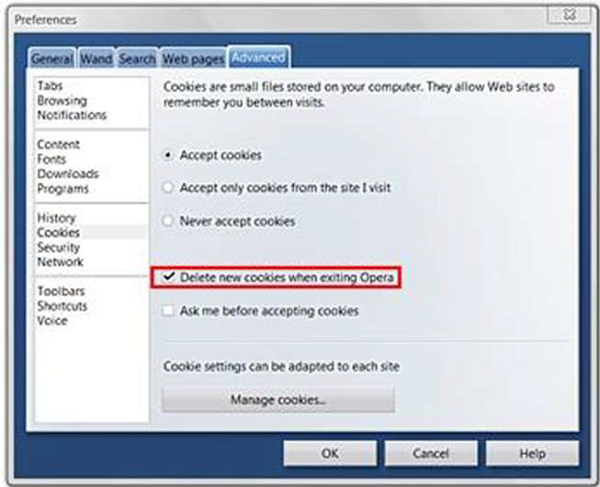
Step 5 − Select 'Delete new cookies when exiting Opera'. If you want to use a specific website but don't want to keep any cookies for that site between your visits, select this option. It is not a good idea to use this option for sites you visit frequently.
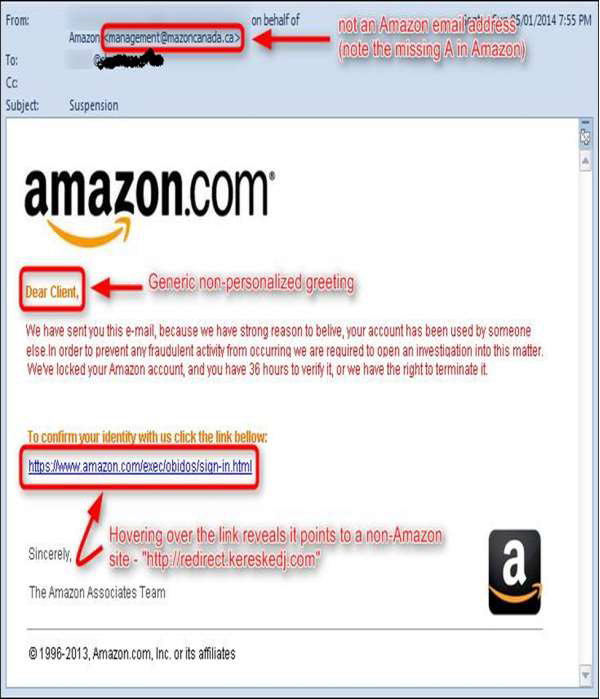
Internet Security - Phishing
Many of us have received similar emails as shown in the following screenshot. They appear as if coming from a genuine source, but in fact if we analyze them a little carefully, they are not. Such emails are called “phishing” because it depends on the users whether they will follow the procedure that the scammer is requesting or if they (user) will delete that email and be safe.
The links in the email may install malware on the user’s device or direct them to a malicious website set up to trick them into divulging personal and financial information, such as passwords, account IDs or credit card details. These techniques are too much in use with cybercriminals, as it is far easier to trick someone into clicking a malicious link in the email than trying to break through a computer’s defenses. Although some phishing emails are poorly written and clearly fake.
How to Detect a Phishing Email?
There are several ways to detect a Phishing Email, some of these methods are discussed here for better understanding.
Spelling and Bad Grammar
Cyber criminals generally make grammar and spelling mistakes because they use dictionary too often to translate in a specific language. If you notice mistakes in an email, it might be a scam.
Links in Email
Links in the email are always with hidden URLs, you don't click on it. Rest your mouse (but don't click) on the link to see if the address matches the link that was typed in the message. In the following example the link reveals the real web address, as shown in the box with the yellow background. The string of cryptic numbers looks nothing like the company's web address.
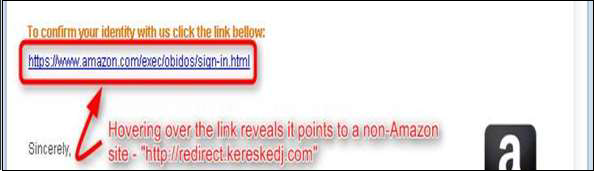
Links also may redirect you to .exe, or zipped files. These are known to spread malicious software.
Threats or They are too Good to be True
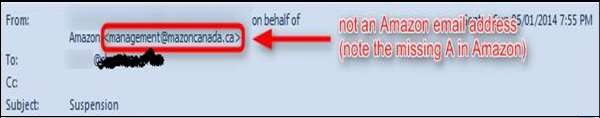
Cybercriminals often use threats that your security has been compromised. The above screenshot shows it very well. In our case the subject talking about Suspension.

Spoofing Popular Websites or Companies
Scam artists use graphics in email that appear to be connected to legitimate websites, but actually they take you to phony scam sites or legitimate-looking pop-up windows. In our case, there is this email of Amazon which is not a genuine one.
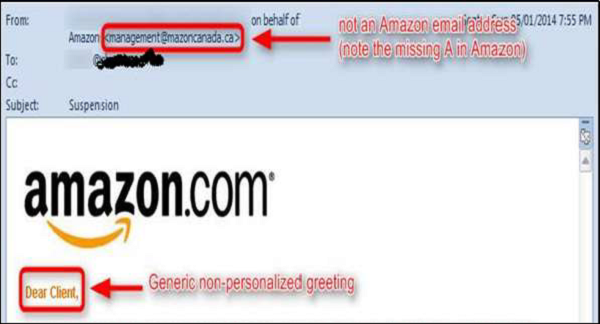
Salutation
Generally, if it is genuine you will have a personalized email like Dear Mr. John, but the cybercriminals, they don’t know your name except the email address, so they will use just a part of your email in the salutation or a general salutation.
Got Phished by Mistake?
What to do in case you think that by mistake, you got phished? In such a case, you can take the following measures −
Change the passwords immediately of the account that you think has been hacked.
Check if any money has been withdrawn or any payment done through your account. You can contact your financial institution directly for this.
Contact the authority on whose behalf you got that email. You should also report to your account administrator.
Internet Security - Social Network
Social Networking is the use of Internet based on social media systems to get in touch with family, friends, customers, classmates, etc. Social Networking can be done for social purposes, business purposes or both. The programs show the associations between individuals and facilitate the acquisition of new contacts.
Social Networking is becoming more and more popular nowadays. For better understanding of its popularity, see the following graph.
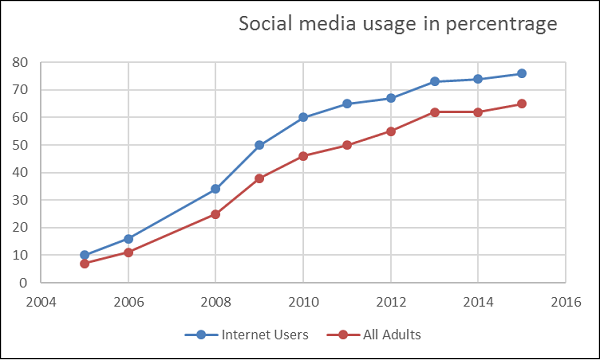
As you can see two thirds of the population are using social media which makes it very attractive for cybercriminals. They can hack an account of others and make profiles for different purposes which can be used as a bridge to attack their social network, or to get their data.
Profile Impersonation
The top threat for year 2015 in social media wasProfile Impersonation. Many of us have seen in Facebook the fake profiles of someone that we know. This generally is made into a phishing link to your known social network. One precaution to avoid such phishing is to report the fake account immediately and let the concerned authorities take action. If you accept the friend request sent by such a fake profile, all your personal photos and other data can be stolen from your account and the hacker can use it in different ways.
Internet Security - Chrome
In this section, we will see the most used explorer from the security viewpoint. What settings should it have in order to minimize the attack surface that can come from visiting different webpages which might be infected.
After installing, we need to secure the Chrome browser by following these steps:
Enable Automatic Update Downloads
Google Chrome automatically updates every time it detects that a new version of the browser is available. The update process happens in the background and doesn't require any action on your part. To check whether there is an update, go toMenu – Help – About Google Chrome.
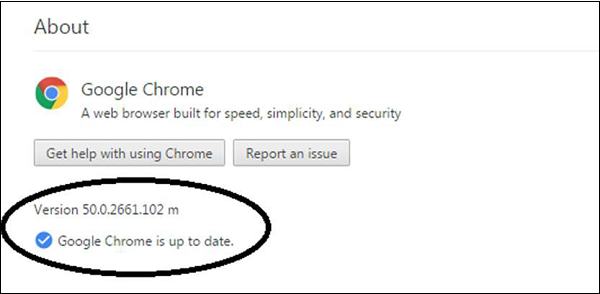
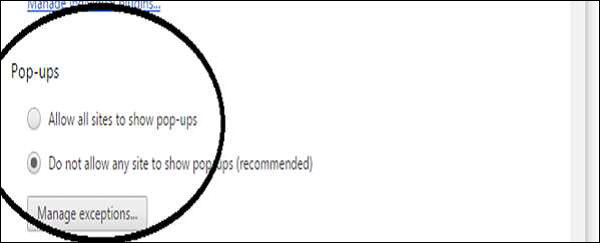
Block Pop-Ups
To block pop-ups, go to Menu → Preferences → Show advanced settings... → click the Privacy/Content Settings button. Scroll down to Pop-ups, chose "Do not allow..."
This setting will block any webpage that wants to show a pop-up without your permission.
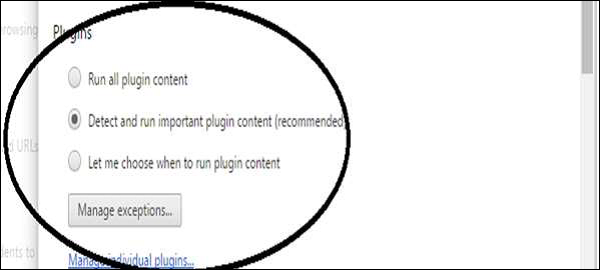
Block Plug-In
To block plug-ins, go to Menu → Preferences → Show Advanced Settings... → click the Privacy/Content Settings button. Scroll down to Plug-ins, chose "Detect and run important...”
This setting sometimes can put the chrome browser at risk.
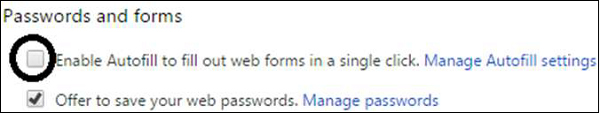
Set your browser to not set passwords
Go to Menu → Preferences → Show advanced settings... → under Passwords and forms, uncheck the "Enable Autofill...
This will help you in a way that if any unauthorized user gains access into your computer, they will not have the chance to auto log in webpages that request your username and password.
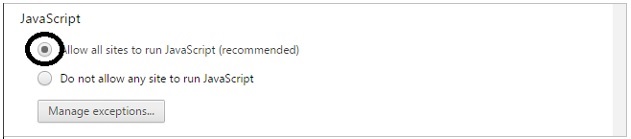
Java/JavaScript
Go to Menu → Preferences → Show advanced settings... → click the Privacy/Content Settings button. Under JavaScript, chose "Allow all sites...
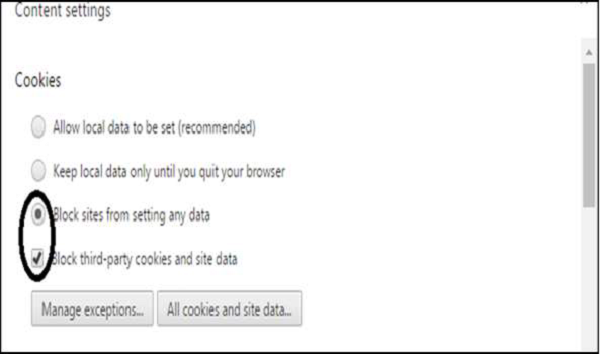
Block Cookies
Go to Menu → Preferences → Show advanced settings... → click the Privacy/Content Settings button. Under Cookies, choose "Block sites..." and "Block third-party...". This will block the cookies to send information to the servers that you don’t trust.
Install Adblock plug-in
To do this, go to menu → Settings → Extensions → Scroll to the bottom → Click “Get more extensions” → search for Adblock → Install AdBlock by getadblock.com which is very good and very effective.

Internet Security - Mozilla
To download the latest Mozilla Firefox browser version, you can click on the following link −
https://www.mozilla.org
Then after installing it, we need to secure the Mozilla browser by following these steps −
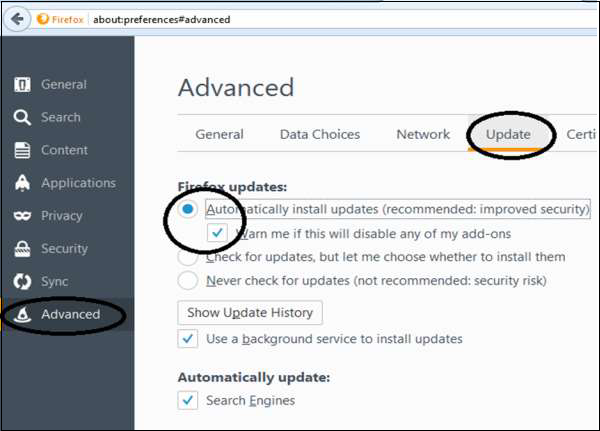
Auto-install the updates
You can auto-install the updates by going to Menu → Options → Advanced → Update Tab. Check all the checkboxes and select “Automatically install…” & “Warn me…”.
Block Pop-ups
To block pop-ups, follow the path Menu → Options → Content. Make sure the first two boxes are checked (Block pop-ups & Load images).

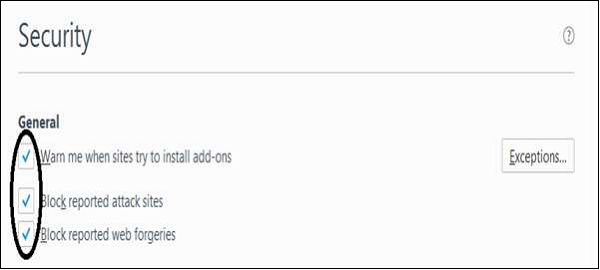
Block add-ons/phishing
Go to Menu → Options → Security. Check the top three boxes that start with “Warn me…” and “Block…”.
Set to forget passwords
Go to Menu → Options → Security. Uncheck the "Remember logins..." box.

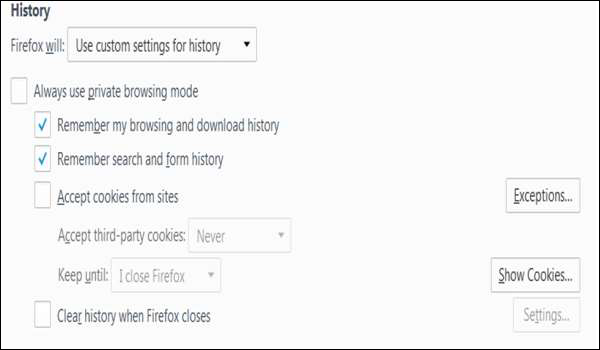
Blocking Cookies
To block cookies, go to Tools Menu → Options → Privacy → History → Check the “Remember..." box under and uncheck “Accept Cookies from sites”.
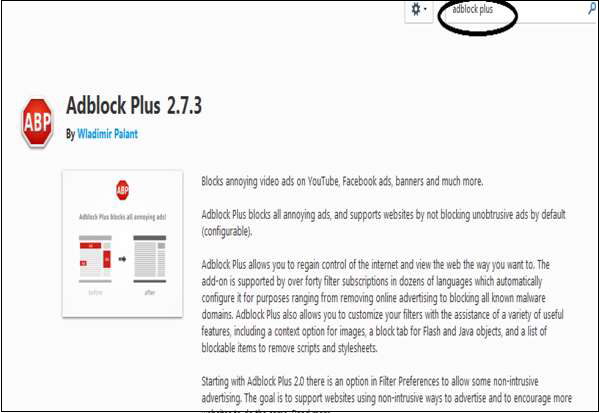
Install AdBlock Plus
Get Add-ons – type Adblock plus created by Wladimir Palant.
Internet Security - Explorer
Internet explorer is the browser of Microsoft and by default is incorporated with Windows OS and doesn’t work on other Operating Systems.
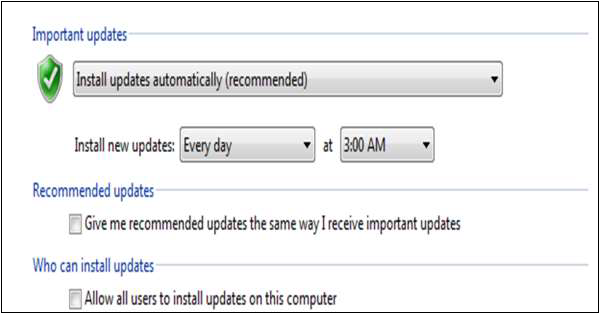
Auto-download Updates
Updates for Internet Explorer are handled by Windows Update located in Control Panels. Set it to Daily updates as shown in the following screenshot.
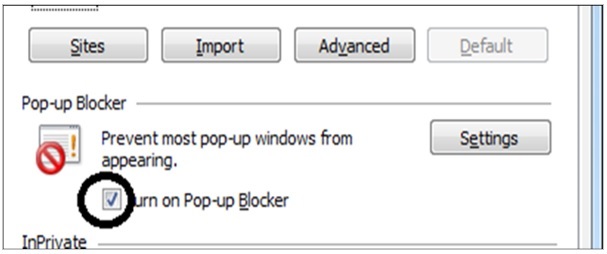
Block Pop-ups
To block pop-ups, go to Tools Menu → Internet Options → Privacy tab and set the slider to MEDIUM. Check the "turn on pop-up blocker” box.
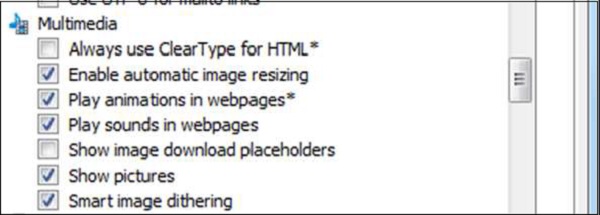
Block Plugins
To block plugins, go to Tools menu → Internet Options → Advanced tab and scroll down to Multimedia. Uncheck Play animations” and “Play sounds” in webpages if they are checked.
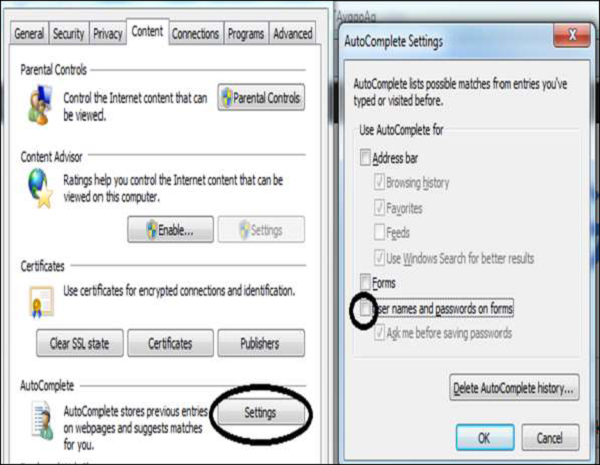
Delete Passwords
Go to Tools menu → Internet Options → Content tab and click the AutoComplete Settings button and uncheck the "user names and passwords..." box.
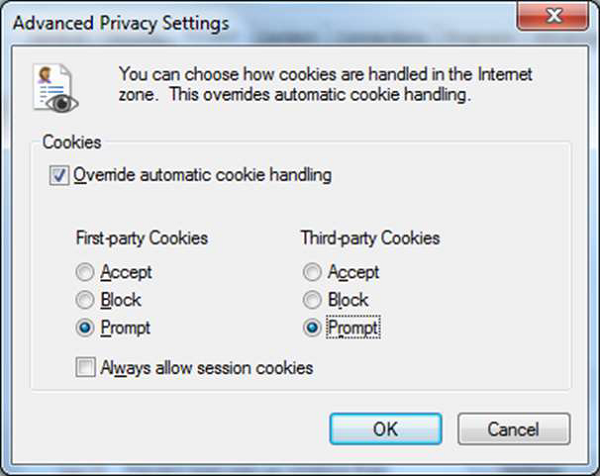
Block Cookies
To block cookies, go to Tools menu → Internet Options → Privacy tab and click the “Advanced” button. Check the “Override” box and the “Accept” button for First-party cookies and “Prompt” button for Third-party cookies. The “Always allow…” button should not be checked. Click OK. When done, click on Apply button.
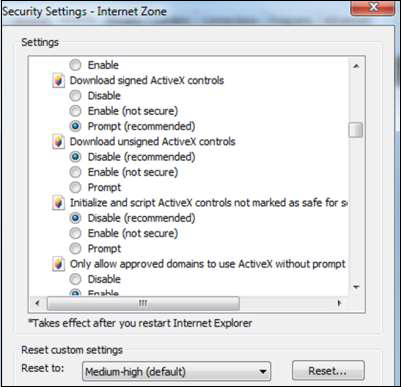
The next step is to go to Tools Menu → Internet Options → Security → Custom level →Download unsigned ActiveX controls → Disable (Recommended).
Internet Security - Safari
Safari is a web browser developed by Apple based on the WebKit engine. It comes included in the iOS and is said to be slightly different from other browsers.
Auto-download Updates
Updates for Safari are handled by System Preferences → Software Update located under the Apple menu. Set to Daily updates.
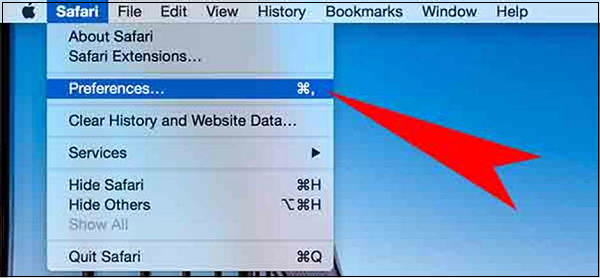
Block Pop-ups
Go to Safari Menu – Preferences – Security tab and make sure the “Block pop-up windows” box is checked.
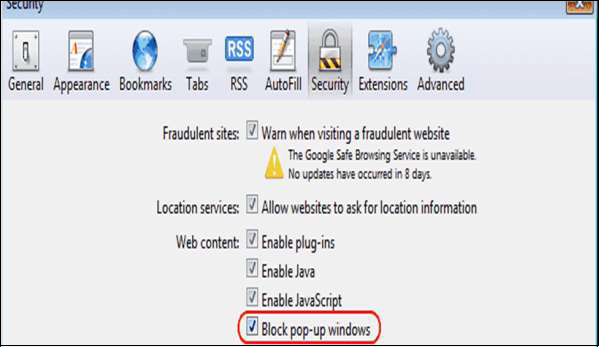
Block Plugins/Phishing
Go to Safari menu → Preferences → Security tab and uncheck the “Enable plug-ins” box.
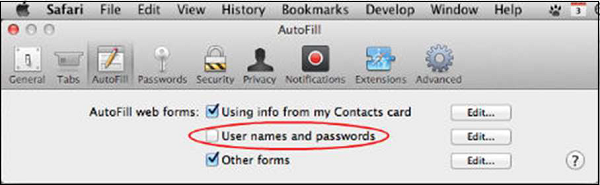
Delete Passwords
Go to Safari menu → Preferences → AutoFill tab and uncheck the "user names and passwords" box.
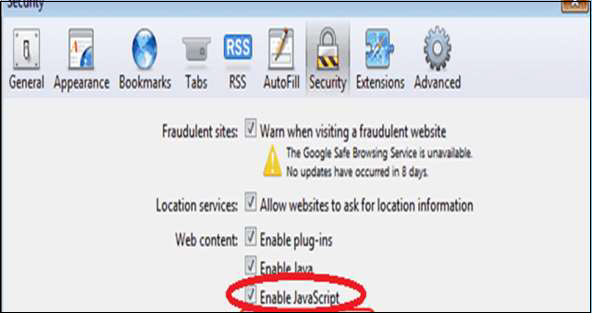
Java/JavaScript
Go to Safari menu → Preferences → “Enable JavaScript” checked.
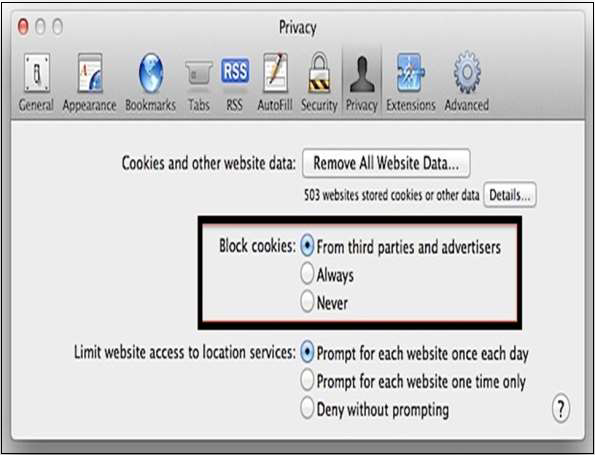
Block Cookies
Go to Safari menu → Preferences → Privacy tab and select “Block cookies: From third parties...”.
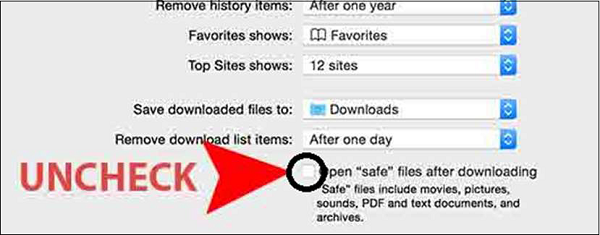
Disable Auto-Open of Open Files
In Safari, you can choose not to open them after downloading, go to the Safari Menu – Preferences – General tab. Uncheck the box that says Open "safe" files...
Internet Security - Gaming
Online games are played over the Internet which can vary from complex graphics to multiple users. They involve many technologies most often use Java, Flash, etc. which is made possible using media streaming for user interaction. In general, online gaming utilizes various forms of socializing like forums, chat rooms, so this interaction with other users that some of them can be malicious may be hackers.
There are different types of online games −
- Single user playing game like Miniclip
- Multiple player games
- Cross-platform online game
- Real-time strategy game like Imperia
- Browser games which utilizes directly the Internet explorers
Risks from Online Games
Nowadays most of the online games are multiple user games and the risk that comes from other users are very high and are as shown below −
Viruses − The player can be attacked from email attachments, phishing or instant messaging. This can result to the hacking of the user computer or the network.
Malicious Software − Attackers can use online games to redirect the genuine users to a fake webpage to steal their credentials.
Hacking that comes from Hacked Gaming Servers − This hacking can come when the server of the game has been compromised because of its vulnerability as a result this can put all the users in danger who are connected to this gaming server.
Insecure Game Coding − This is another type of known vulnerability where all the data of users like name, surname, credit card information can be stolen because of an insufficient security on the programing code.
Social Risks
This risk comes from social interaction with other malicious users who want to steal your data which can be −
- Your personal Information
- Credit card details
- They can pretend to be a child and contact other children asking them to reveal other information.
Threats in Online Gaming
Threats at games are of different types and for different purposes which can be to gain unauthorized access to play the game generally. This technique is done by stealing others’ password.
A few other very often used techniques are −
- Dictionary attack
- Social engineering
- Malware infection
- Corruption the genuine authentication software
- Phishing user ID and password by sending emails.
Hackers can cheat at the game for the purpose of −
- Stealing virtual property
- To obtain higher levels of plays
- Corrupting the gaming software which controls the levels of play
- Skipping the policies
- For making DoS to the gaming provider.
- Paying for the game by using Trojans to hack and steal the Card ID and other details
What to do for secure online game playing?
- Encrypt critical game data
- Minimize client’s data
- Create a security tutorial for the players
- Complex password policy
- Audit trails and logs
- Patching bugs
- Always use an antivirus software on your computer.
- Be prudent when opening files and links sent by other users over instant messaging of game.
- Validate authenticity of the new release of software’s.
- Create complex passwords.
- Update your computer. Connect securely with your browser.
You are welcome to comment your suggestions regarding this post.
Follow for more.
See also.:--






































